Appearance
Cloudflare Integration
Realm Security can collect log data from an S3 bucket, or logs can be sent directly to Realm via an HTTP endpoint logpush
AWS S3
Setup AWS
In this step, you will be provisioning necessary infrastructure in AWS Console for the following purpose:
- Create S3 Bucket to collect cloudflare logs
- Create SQS Queue to receive notifications when new logs are written to the S3 bucket
- Update S3 bucket properties to send notifications to the SQS queue
- Create and attach a policy to allow AWS S3 service to send notifications to the queue
- Create a Realm IAM user with permission to read from the Cloudflare S3 bucket and notification SQS queue
- Create AWS Access Key and AWS Secret Access Key for Realm IAM user
Create S3 Bucket
- Go to S3
- Create Bucket
- Fill out details
Name: rlm-cloudflare-logs
- Copy the ARN of the bucket
Create SQS Queue for notifications
- Go to SQS Queue
- Create Queue
- Fill out details
Name: rlm-cf-event-notifications
- Copy the ARN of the queue
Create IAM policy
- Go to IAM > Policy
- Create Policy
- Click JSON
- Paste the following and replace s3_bucket_arn with the name of your s3 bucket and sqs_queue_arn with the SQS queue from above
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "s3ReadObjects",
"Effect": "Allow",
"Action": [
"s3:ListBucket",
"s3:GetObject"
],
"Resource": [
"<s3_bucket_arn>",
"<s3_bucket_arn>/*"
]
},
{
"Sid": "sqsEventNotifications",
"Effect": "Allow",
"Action": [
"sqs:ReceiveMessage",
"sqs:DeleteMessage"
],
"Resource": [
"<sqs_queue_arn>"
]
}
]
}- Click next.
- Enter policy name: rlm-s3-notifications-and-read
- Enter description: Grant read access to s3 cloud trail bucket as well as receiving s3 notifications from the SQS queue.
- Click Create Policy.
Create User with credentials
- Go to IAM > Users > Create User
- Enter Name: rlm-cf-s3-read-user
- Click Next
- Click Attach Policy Directly
- Select the policy created in the previous step
- Click Next
- Click Create user
- Select the user that was just created
- Copy the ARN of the user, and save it to a safe location - you will need it in the next step
- Go to Security Credentials
- Click Create Access Key
- Select Third party Service
- Check the confirmation checkbox
- Click Next
- Enter description: Credentials for Realm.Security to read Cloudflare logs from S3 bucket
- Copy and save the Access Key and Secret access key in a safe location, you will need to paste these two values in Realm console when configuring the S3 input feed.
Update SQS policy
- Go to SQS Queues
- Select the rlm-cf-event-notification queue
- Go to Queue Policies > Edit Access policy
- Replace the policy JSON with the following
{
"Version": "2012-10-17",
"Id": "__default_policy_ID",
"Statement": [
{
"Sid": "Stmt1737666508309",
"Effect": "Allow",
"Principal": {
"Service": "s3.amazonaws.com"
},
"Action": "sqs:SendMessage",
"Resource": "<sqs_queue_arn>"
},
{
"Sid": "Stmt1737666814690",
"Effect": "Allow",
"Principal": {
"AWS": "<iam_user_arn>"
},
"Action": [
"sqs:ChangeMessageVisibility",
"sqs:DeleteMessage",
"sqs:ReceiveMessage"
],
"Resource": "<sqs_queue_arn>"
}
]
}- Click Save
Configure notifications for S3 bucket
- Login to AWS console
- Go to S3 buckets
- Select the cloudflare log bucket
- Go to Properties
- Go to Event Notifications and click on Create Event Notification
- Fill out the event notification details
Event name: RlmCFCreateEvents
Select All object create events checkbox
Destination: Select SQS Queue
In the drop down, select SQS queue that you created in the step above
- Click Save Changes
Setup Cloudflare
In this section, you will configure Cloudflare to export logs to S3 bucket created above.
Logpush
Select Analytics & Logs > Logpush. 
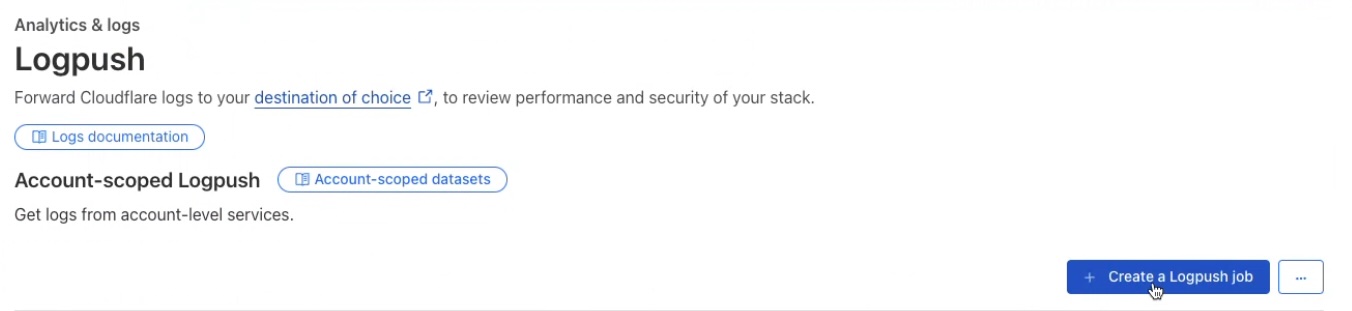
Create Logpush job
Select Destination
Select Amazon S3 object storage 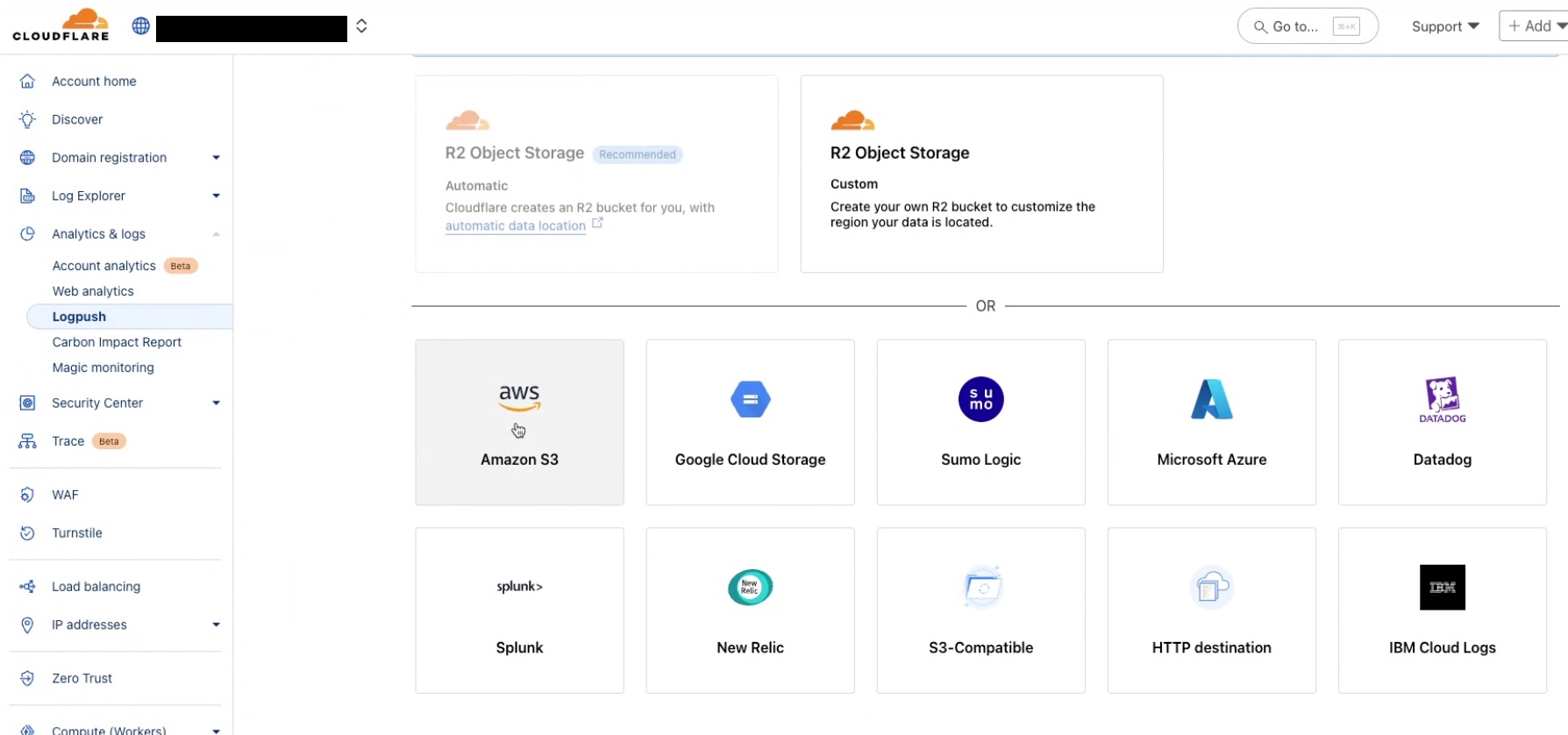
S3 Bucket Details
Enter details for AWS S3 bucket where logs will be forwarded to. 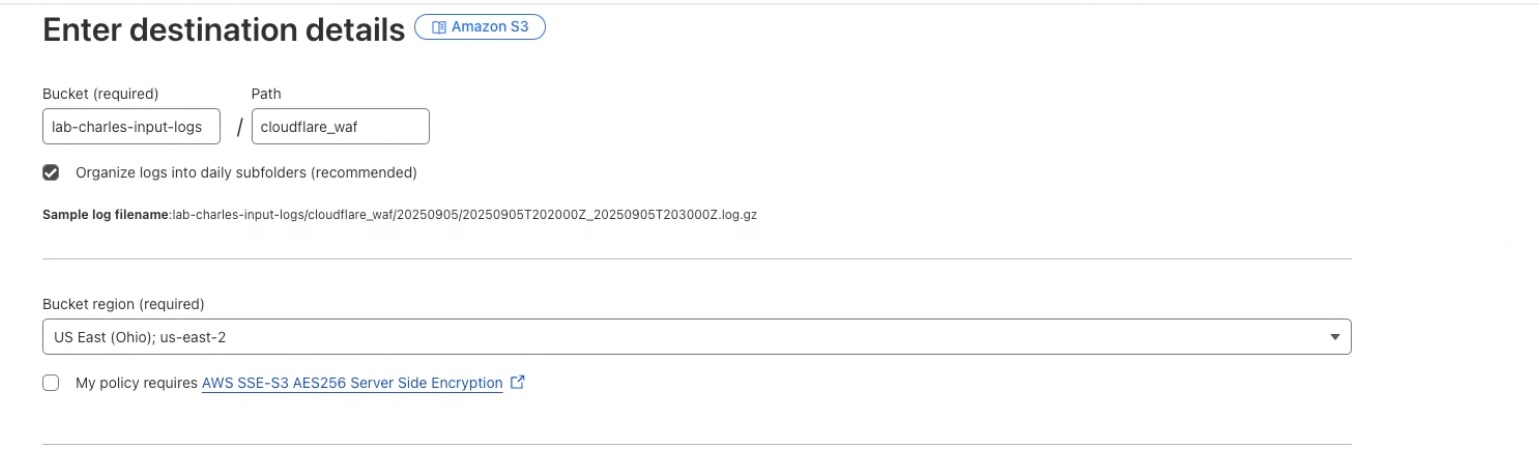
S3 Bucket Permissions
Copy S3 bucket permissions from Cloudflare console and add it to the bucket in the AWS console. 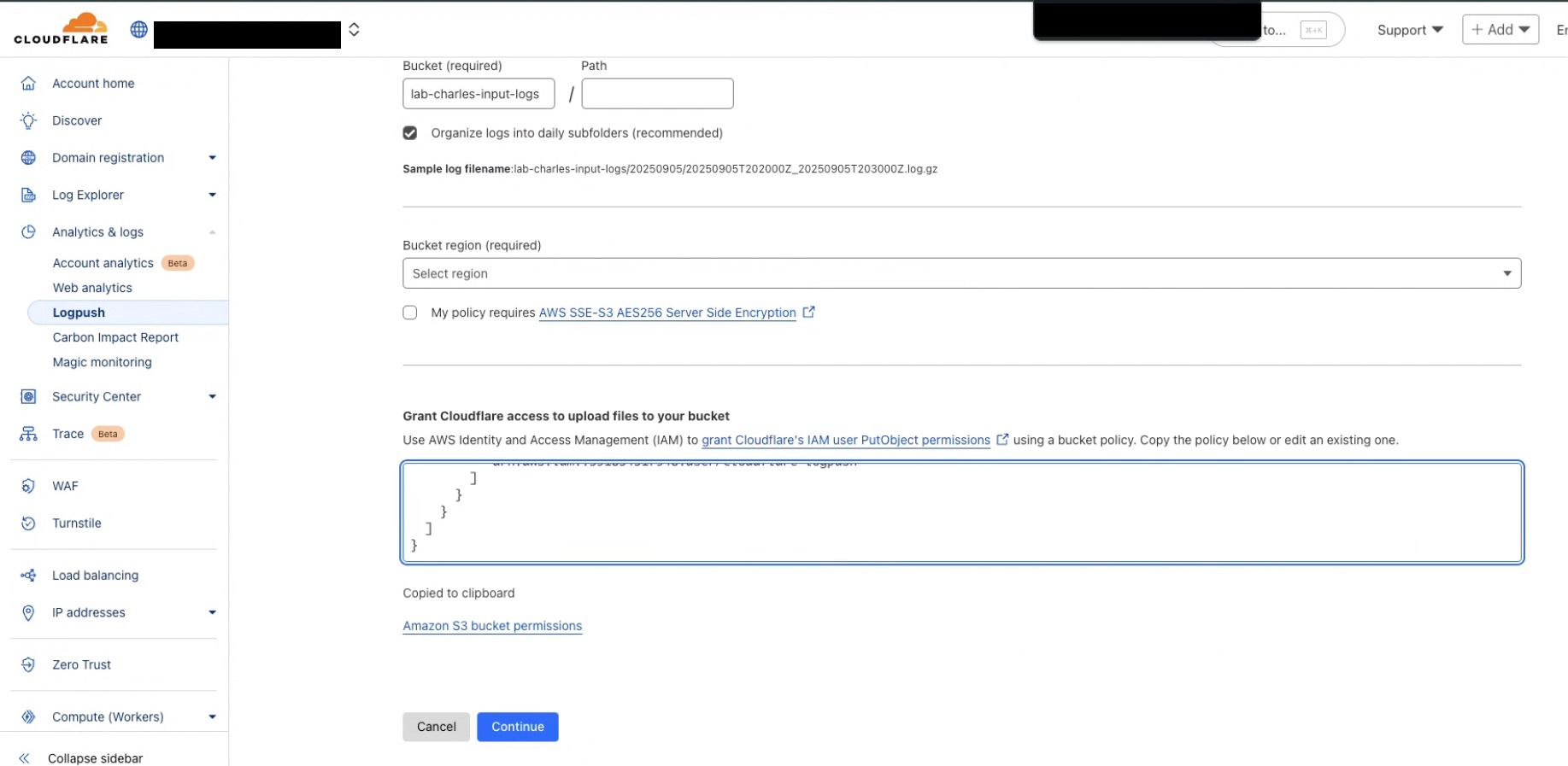
Click Continue.
At this point, Cloudflare will write a ownership challenge text file to the S3 bucket.
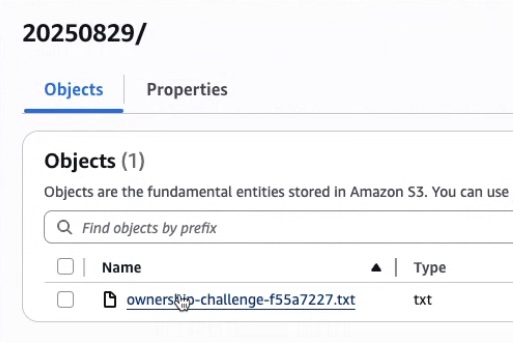
Copy Ownership Token
In AWS console, go to the S3 bucket, locate and open a file called ownership-challenge-xxxxxxx.txt. Copy the contents of the file.
Paste Ownership Token
Go to Cloudflare console and paste the ownership challenge token in the box provided.
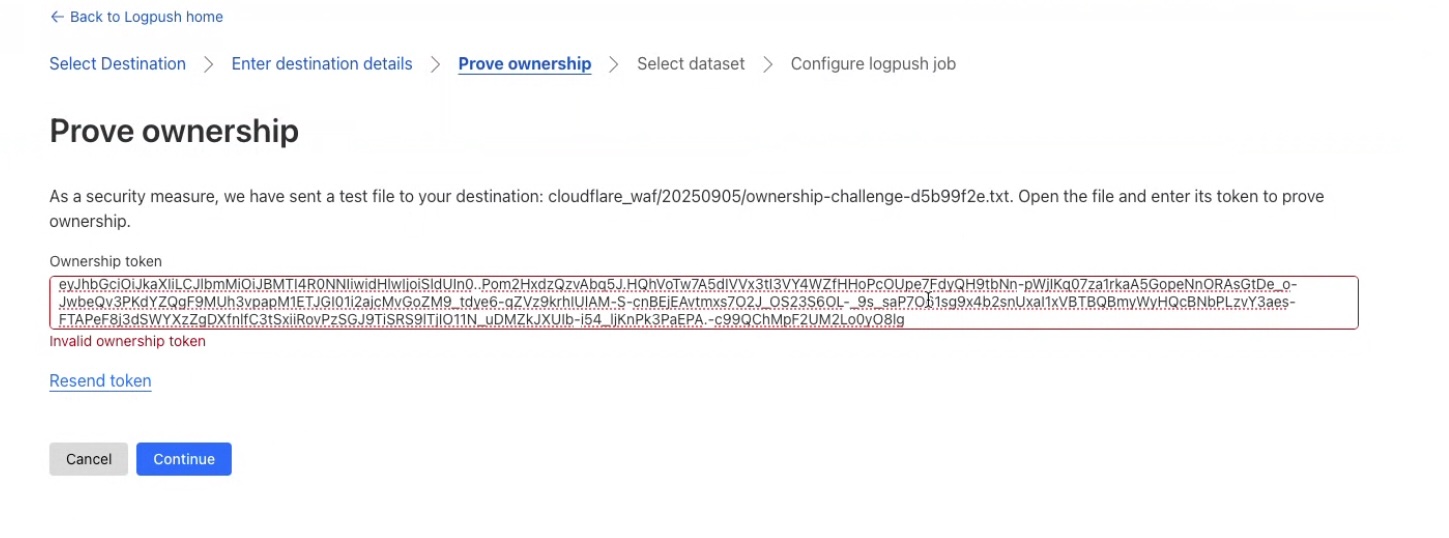
If all goes well, you should see a verification success message.
Select Dataset
Select one or more log datasets to push to S3 bucket. 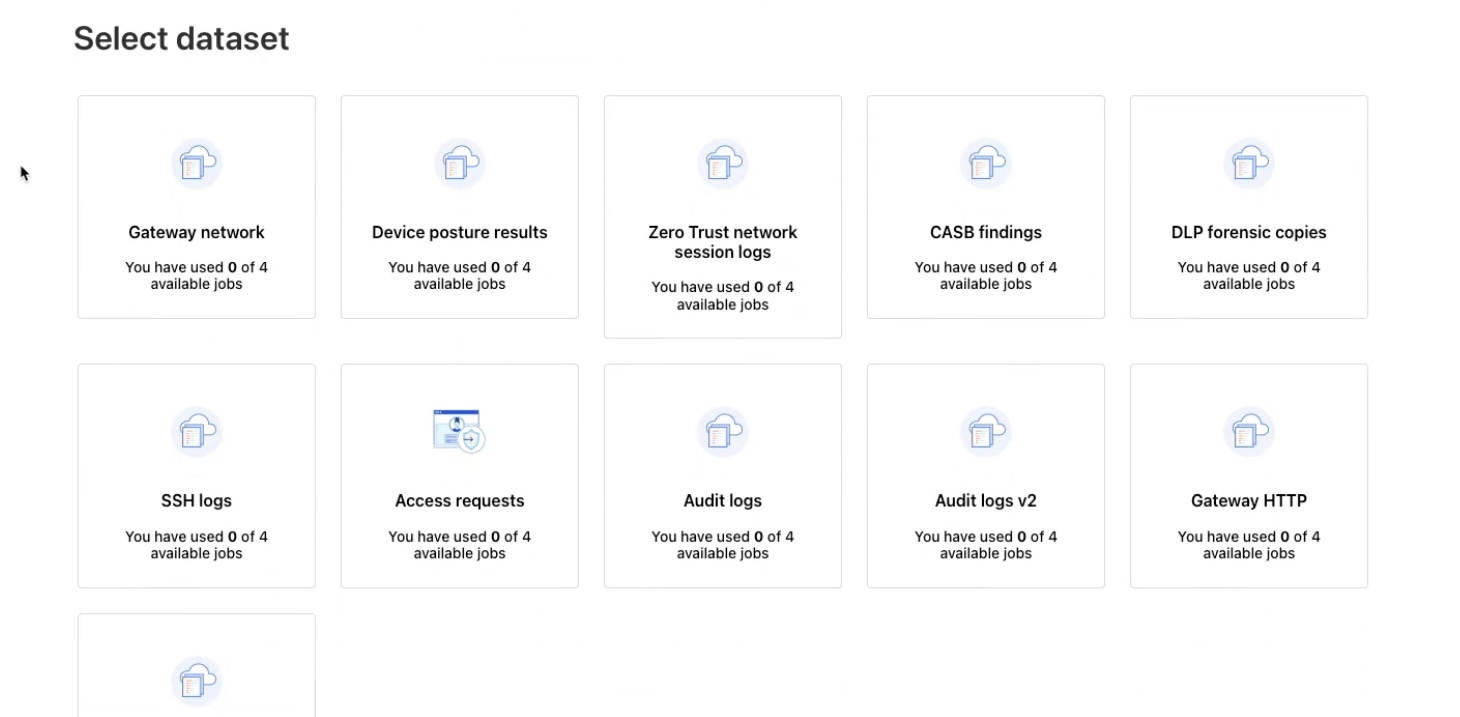
HTTP Logpush
Read more about configuring an HTTP logpush in the Cloudflare Documentation
Prerequisites
- Administrative Access to the Cloudflare Dashboard
- Realm Cloud HTTP input feed
- Make sure to use a Public Certificate and take note of the Authentication Token
Setup Cloudflare
Logpush
Select Analytics & Logs > Logpush. 
Create Logpush job

Select Destination
Select HTTP destination 
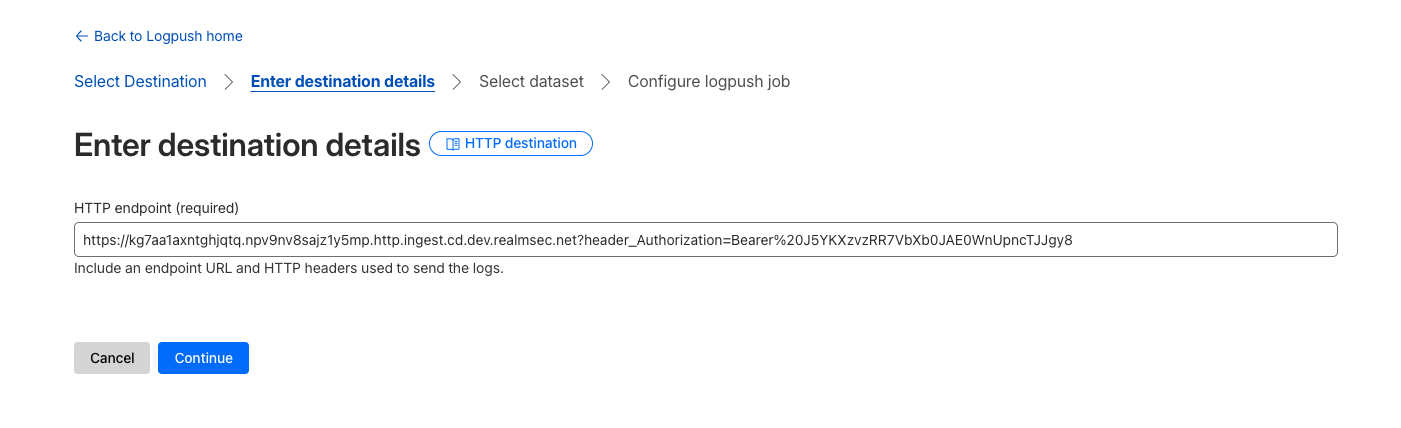
Enter HTTP Input Feed details
Enter the URL(including https://) of the Cloud HTTP input feed, and make sure to include the authentication header at the end of the URL like so: https://my-url.http.ingest.cd.dev.realmsec.net?header_Authorization=Bearer%20<token>