Appearance
Ingesting logs from Sumo Logic
Realm supports ingesting logs from Sumo Logic. While this is not a typical setup our customers leverage in Production, it is useful during POCs.
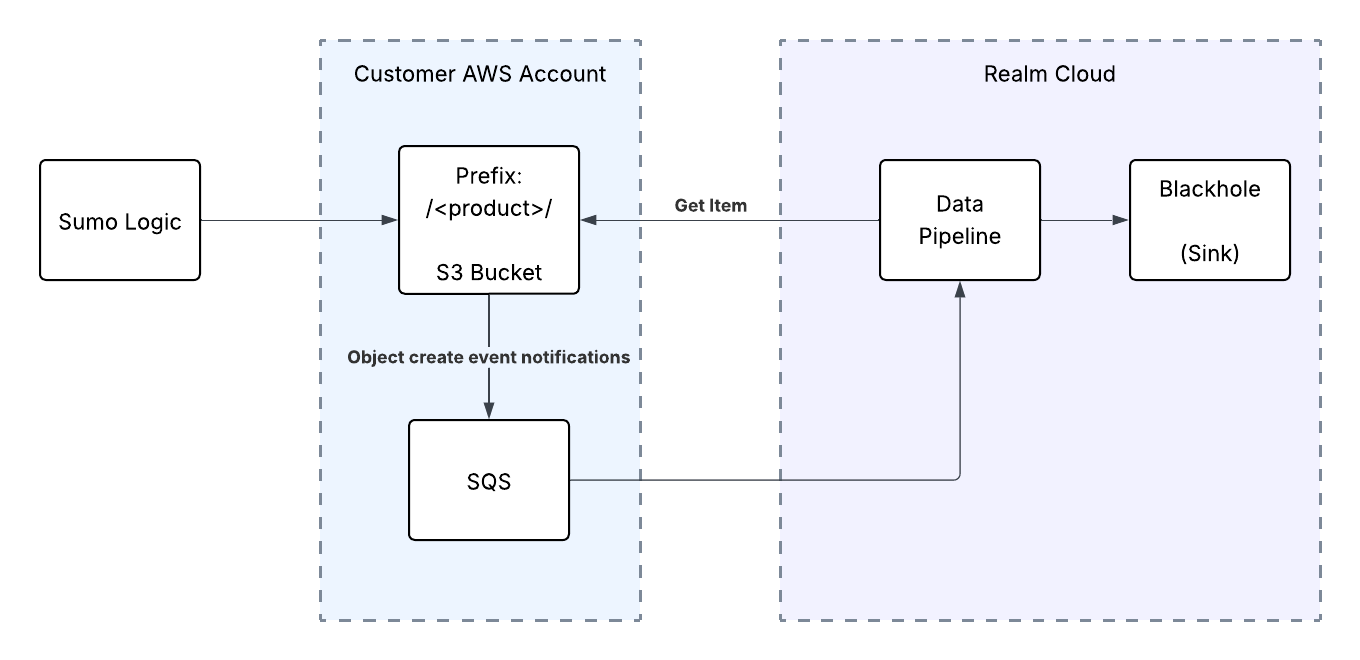
The integration involves following steps
- Step 1: AWS Console: Create S3 Bucket & Role for Sumo Logic
- Step 2: Sumo Logic: Setup Data Forwarding in Sumo Logic
- Step 3: AWS Console: Setup Bucket Notifications & SQS Queue
- Step 4: Realm Console: Setup Source
Step 1: AWS Console: Setup S3 Bucket and Role
In this step, you will set up a S3 bucket & Role for Sumo Logic to forward the data to.
Setup S3 bucket
Login to AWS console,
- Go to S3
- Click
Create bucket
Setup IAM Policy
Setup an IAM policy that grants read and write permission to the S3 bucket. Login to AWS console
- Go to IAM > Policies
- Click
Create Policy - Copy & paste the following JSON, remember to replace
<bucket_name>with the name of the bucket created above.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowS3Writes",
"Effect": "Allow",
"Action": [
"s3:PutObject",
"s3:GetObject",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::<bucket_name>",
"arn:aws:s3:::<bucket_name>/*"
]
}
]
}- Give it a name and Save policy
Create IAM Role
Create an IAM role that gives cross account permission to Sumo Logic Account Id.
- Go to IAM > Roles
- Click
Create Role - Select
AWS Account - Select
Another AWS Account, enter account Id provided by Sumo Logic - Select
Require External ID - Enter external Id provided by Sumo Logic
Note: To get Sumo Logic Account Id and ExternalID, Login to Sumo Logic console, Data Management > Data Forwarding > Add Destination. Copy AccountID and External ID from the destination popup.
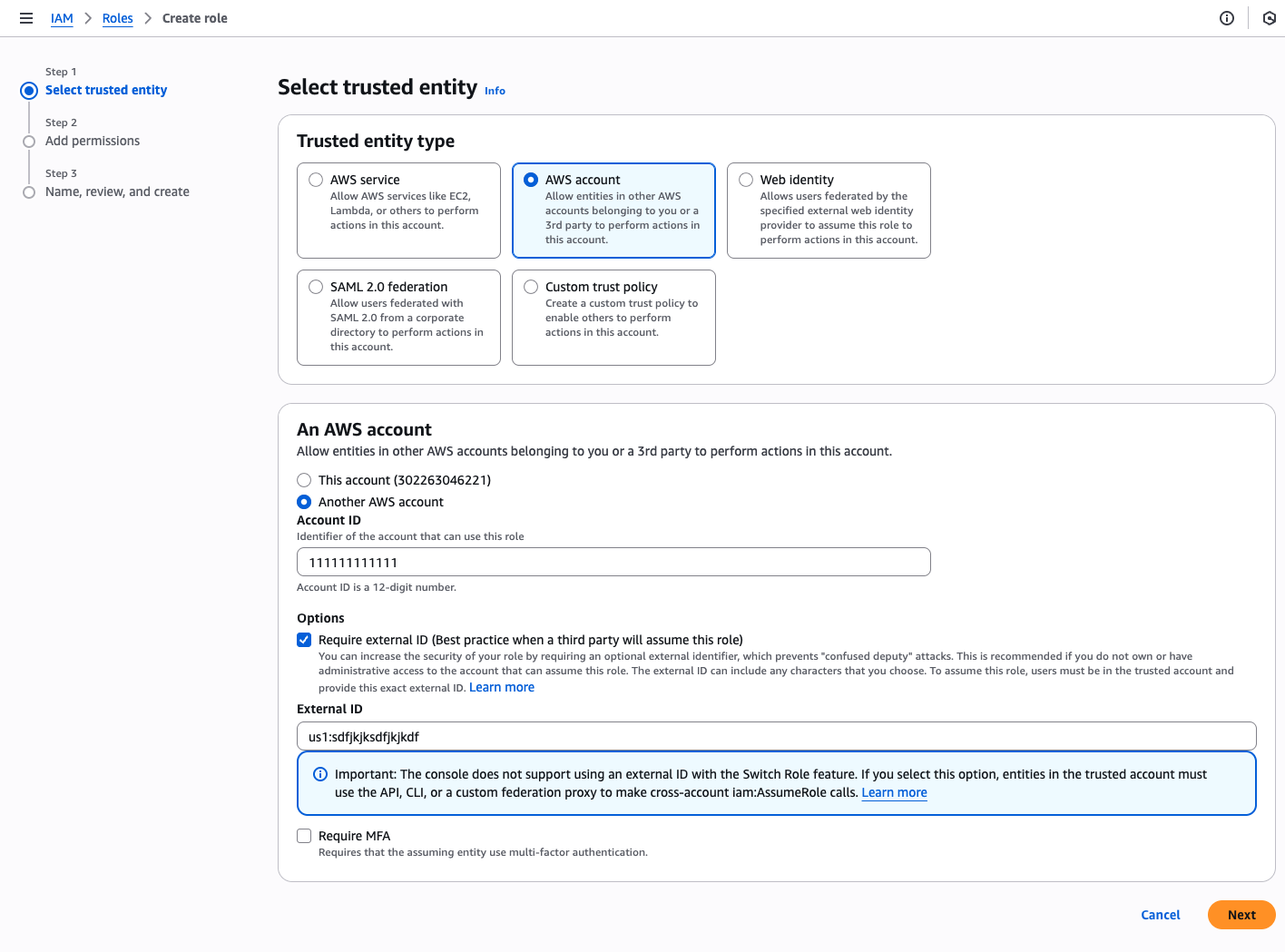
- Click Next
- Search for the policy created in the above step
- Select the policy, Click Next
- Give the role a name for ex:
sumo-fortigate-s3
Step 2: Setup Data Forwarding in Sumo Logic
Add Data Forwarding Destination
In Sumo Logic console
- Data Management > Data Forwarding
- Click
Add Destination - Enter the name of the S3 bucket created above
- Enter the region where the S3 bucket was created
- Enter the arn of the role created above
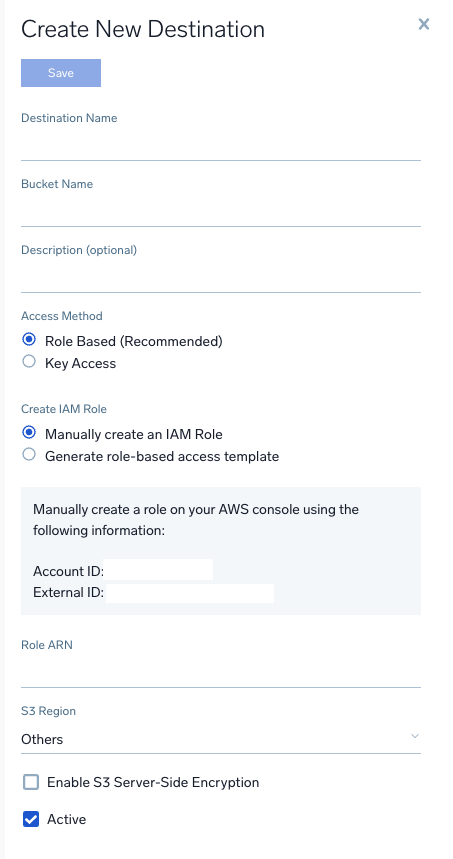
Forward Partition Data to S3 Destination
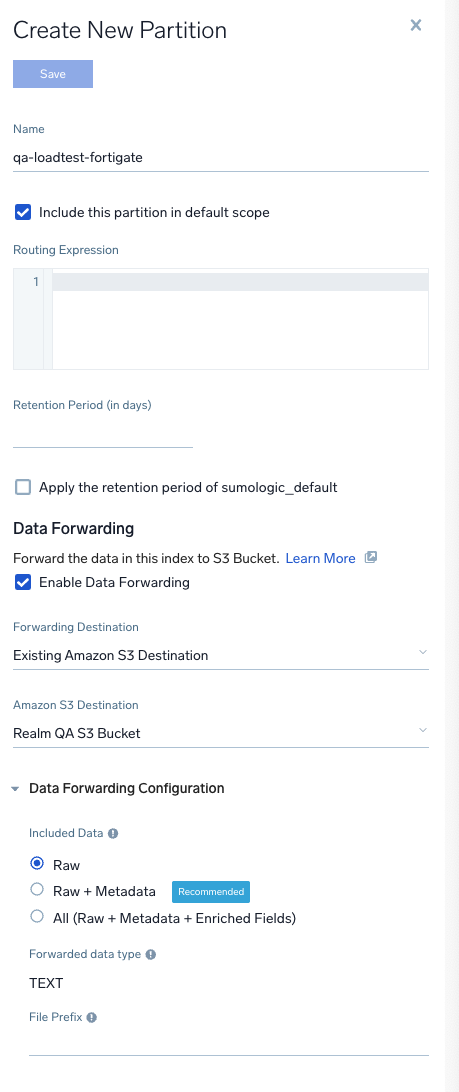
In Sumo Logic console
- Data Management > Partitions
- Select the partition that would like to configure Data forwarding for.
- Enable Data Forwarding for the partition
- Select Forwarding Destination:
Existing Amazon S3 Destination - Select Amazon S3 Destination:
<destination_created_above> - Included Data:
Raw - Forwarded data type:
TEXT - File Prefix:
<product_name>/
Note: Please make sure the prefix ends with
/, it ensures that all logs for the partition will be saved to a "product name folder" in S3.
Step 3: AWS Console - Setup Bucket Notifications & Keys
Follow these instructions to setup SQS queue, bucket notifications and keys that will be required in the next step when configuring an input feed in Realm console.
Step 4: Realm Console: Setup Source & Destination
Add a Source
Login to Realm Console,
- Go to Sources
- Click
Add Source - Select a product eg: Fortigate
- Select Create new source
- Give it a name
- Select Transport Method:
AWS S3 - Enter the credentials and arn of the SQS queue
- Update name of the input feed to
<source_name>-S3eg:Fortigate - S3 - Click
Save
Add a destination
- Go to Destinations
- Click Add Destination
- Select Intended Use:
SIEM - Give it a name eg:
SIEM - Click
Add
Add Blackhole output feed
- On the SIEM Destination page, Click Add Output feed
- Give it a name: Blackhole
- Select Type: Blackhole
- Click
Add
Connect Source to the Destination
- On the SIEM Destination page, Click Add Source
- Select a source from the drop down: eg: Fortigate
- Click
Add